Magnet Graykey can offer similar-day use of the most recent iOS and Android units – often in less than one hour.
Don't carry your Social Security card inside your wallet. Instead, store it in a safe position in your house. Endeavor to memorize your variety and that means you don't should just take your card out every time you're filling out a document that requires it.
They're mainly constructed by scraping the general public-dealing with area of platforms working with automated programmes to consider whatever information and facts is freely readily available about users.
When you’re locked out as the results of a hack, you are able to restore Twitter account obtain straight through the System.
Create your account, We'll assign your marketing campaign to the new Social Community Account Manager and request a handful of questions on the kind of followers you want to obtain.
Organizations deliver her items, she encourages them to her massive pursuing, and he or she receives compensated. It’s a simple task, but one which grew to become considerably more challenging when her Fb was not long ago hacked.
Our service is meant to enhance your online existence and visibility by way of different digital marketing and advertising approaches. We leverage a massive world network, which includes Local community teams, marketing and affiliate networks, influencers, cellular apps, and immediate partnerships. RiseKarma’s Superior AI algorithm, up-to-date weekly, makes certain that you’re achieving the proper audience with your focus on market place.
Unusual Posts or Messages: If you see odd points posted or despatched from the accounts that you choose to didn’t do.
You might be chargeable for producing staff security. How could you be certain they're Prepared for emergencies?
28. With accounts getting so difficult to recover, cyber safety providers have even started offering services to aid consumers get the job done with Social Media platforms that can help Get well their accounts.
By choosing a slower shipping and delivery velocity over the payment course of action, you are able to receive followers at your chosen speed and pause just after acquiring the desired number of more info followers.
Applications like Axiom have allowed examiners to streamline their workflows and cut through the electronic sound to locate, Get well, and gather evidence a lot quicker.
This mixture of abundant facts and weak safety creates the perfect ecosystem for hacking. Till oversight enhances and people turn out to be much more cautious about sharing, social media will stay very susceptible to breaches – often with lifetime-altering repercussions for unsuspecting people.
Having said that, we offer a free refill service included in all our deals to interchange any followers who unsubscribe, ensuring that your follower count stays reliable.
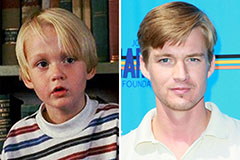 Mason Gamble Then & Now!
Mason Gamble Then & Now! Marla Sokoloff Then & Now!
Marla Sokoloff Then & Now! Robbie Rist Then & Now!
Robbie Rist Then & Now!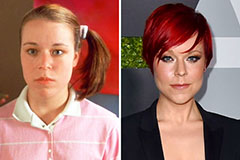 Tina Majorino Then & Now!
Tina Majorino Then & Now! Catherine Bach Then & Now!
Catherine Bach Then & Now!